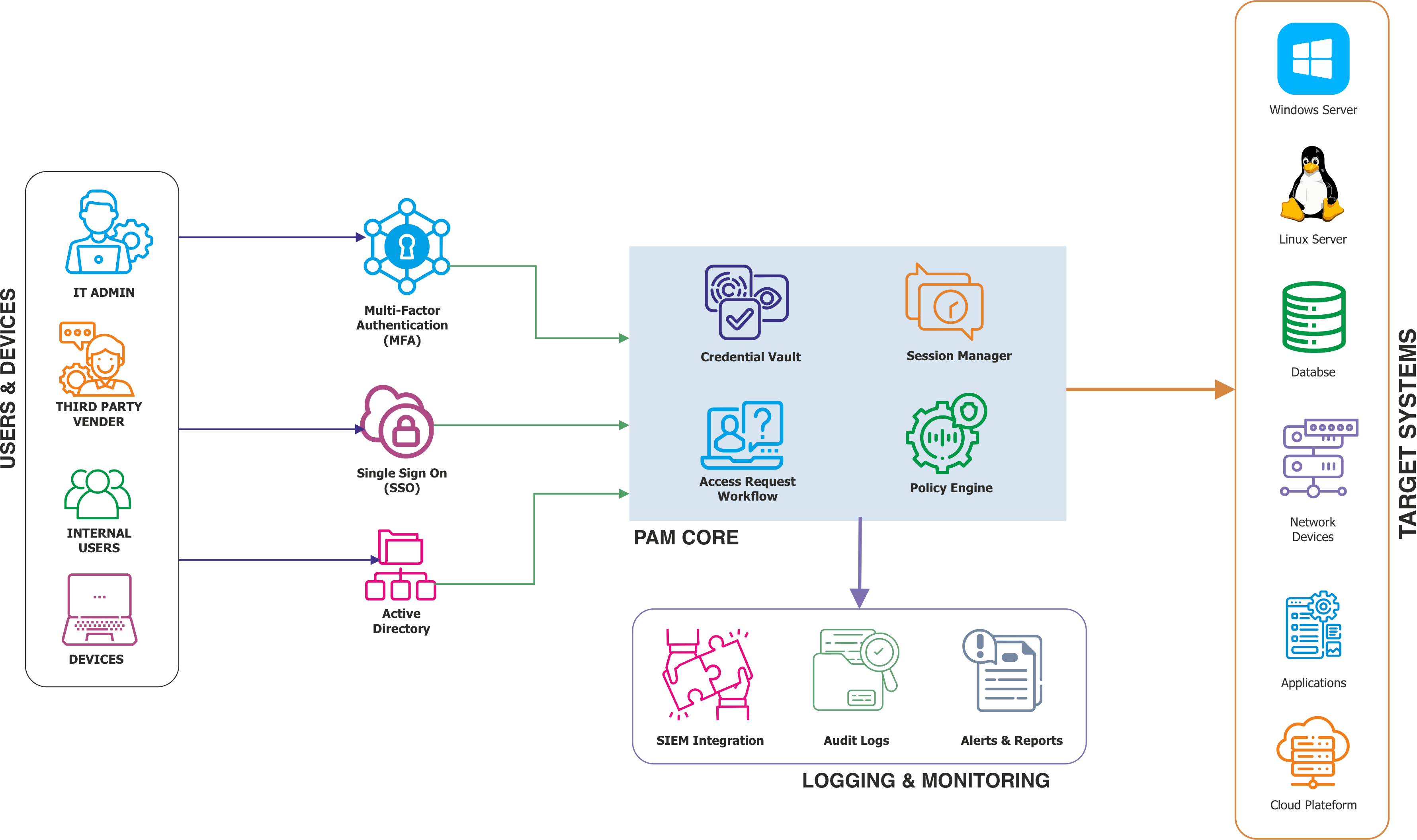
ARCON | PAM offers a range of core features and functionality required to attain a PAM maturity model. A full-blown solution with scalable architecture ensures impregnable privileged identity security. Banking organizations, government agencies, healthcare chains among many vertical markets trust ARCON | PAM for building robust IAM and compliance framework